DLL Hijacking in Cybersecurity
Table of Contents
- DLL Hijacking in Cybersecurity
- Procedure for the Attack
- How to identify a DLL Hijacking Attack
- Countermeasures for DLL file Hijacking
- Update antivirus Software
- Educate employees on the risks of phishing and social engineering
- Boost your security posture
- Set up a vendor risk management system
DLL files, or Dynamic Link Library files, store the resources that an application needs to execute. Images and a library of executable functions are examples of what might be included. End-users cannot open DLL files; only the related application may do so, which normally occurs when the application starts up. DLL files are required by Windows systems in order for them to understand how to best utilize their resources, host computer memory, and hard disc space.
Because a single DLL file may execute several applications, a DLL hijacking attack might compromise multiple apps. DLL hijacking isn’t a new type of cyber-attack. Since the release of Windows 2000, it has been in circulation among hackers. Hijacking of Dynamic Link Libraries (DLL) is a sort of cyber-attack in which hackers replace a legitimate.dll file with a malicious one. When the application uses this damaged file, it produces incorrect results, as designed by the hacker.
Top Names in Cybersecurity
Procedure for the Attack
- In this attack, the hacker uses social engineering or any other means to exploit the static location where the DLL files are stored and replaces the original DLL files with the malicious.dll file.
- The next time the application runs (either as a result of the hacker’s persuasion or for legitimate reasons), it looks for the required DLL file.
- It looks in the same folder as the program folder first, then searches based on the operating system’s priorities. The hacker might get the desired effect (admin rights) on the victim’s PC as soon as this malicious file is picked up and loaded.
How to identify a DLL Hijacking Attack
Windows’ Process Explorer (Procmon) can assist you to find out whether a DLL hijacking attack is going on.
Process Monitor displays all of the file systems that are being loaded in real time. You can see if any foreign DLL files are being loaded instead of the originals by using the relevant filters.
Step 1: Download and run Windows Process Explorer.
Step 2: Look for the program that may have been the victim of a DLL hijacking attempt.
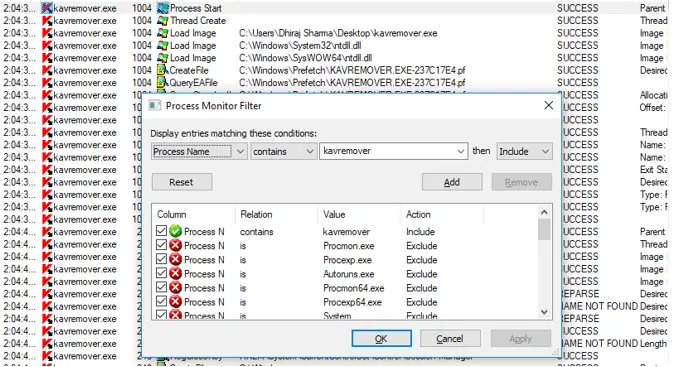
Step 3: Filter the results to only show DLL files.
In Process Explorer, use ctrl + L to apply a filter. Set the filter to only show active files with a.dll extension in their path.
Click add.
Click apply.
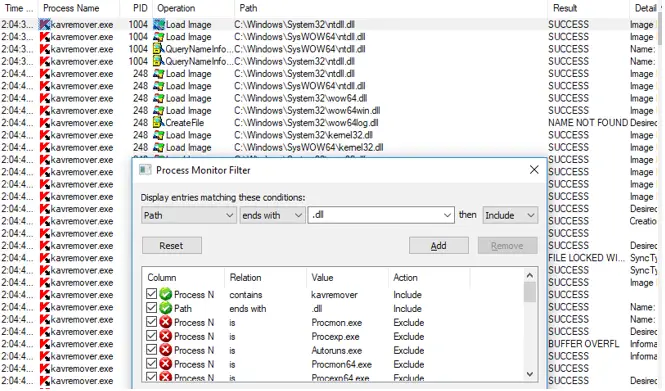
Step 4: Apply the following filter to the directory: name could not be found
You should create a filter that recognizes DLL files that have been loaded from the internet. Because the majority of DLL hijacking occurs when a foreign DLL file is loaded instead of the system’s native version.
These files are marked as FILE NOT FOUND in Process Monitor.
To use the filter, hold down Ctrl + L and enter the following parameters:
The result is NAME NOT FOUND
Click add.
Click apply.
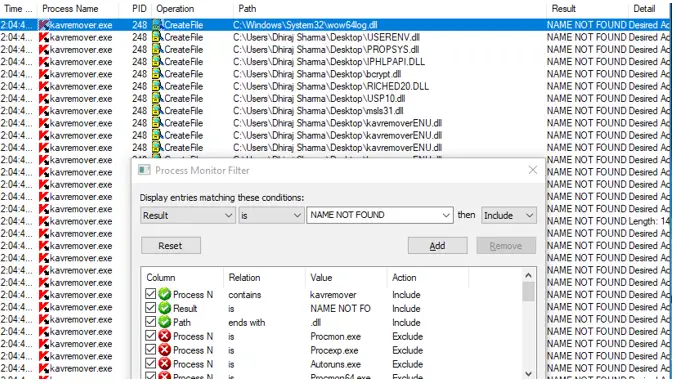
The list that appears shows all of the DLL files loaded outside of the system directory by the specified application.
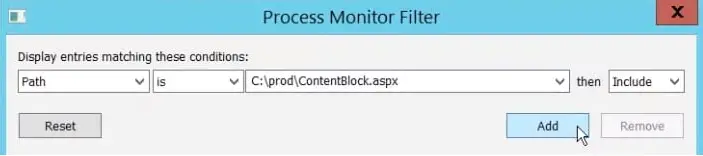
The malicious Windows DLL file will be in the same directory as the victim application. Apply an extra filter to only display DLL files in the Application’s directory to investigate this option.
Set the following criteria by pressing Ctrl + L:
Path is [Path address]
Click add.
Click apply.
Countermeasures for DLL file Hijacking
Software engineers are responsible for establishing the initial line of defense. To prevent Windows from defaulting to its DLL search path protocol, developers must use safe coding techniques and indicate the actual location of all linked DLL files. Programmers should utilize an absolute path instead of a relative path. Turn on the router firewall and use a hardware firewall. An Intrusion Detection/Prevention System can also aid in the prevention of such attacks. There are a number of third-party tools that can assist in determining if a program is vulnerable to DLL Hijacking attacks.
Because compliance with secure coding methods can never be guaranteed, businesses should employ the following additional safeguards:
Update antivirus Software
Although highly advanced supply chain assault strategies may evade detection by antivirus software, malicious DLL injection attempts are frequently recognized and prevented.
It is critical to maintain antivirus software up to date in order for its detection algorithms to remain accurate.
DLLSPY is a powerful DLL hijacking protection tool that can also identify privilege escalation flaws. This application may be found on GitHub.
Educate employees on the risks of phishing and social engineering
Only if a malicious DLL file is introduced into an ecosystem is DLL hijacking conceivable. DLL hijackings can be avoided if the probability of such an injection is minimized.
The majority of loaded DLL and malware injections come as a result of unwitting staff workers introducing them into an ecosystem. Staff should learn to recognize the warning signs of social engineering and phishing attempts and follow the best security measures to avoid this.
The following are some examples of best practices:
- Creating a user-friendly Information Security Policy.
- Making multi-factor authentication mandatory.
- Before responding with questionable communications, refer them to important staff members.
Boost your security posture
You can rapidly detect any weaknesses within your ecosystems that put your enterprise in danger of DLL hijack attacks by continually monitoring your attack surface.
Set up a vendor risk management system
Unfortunately, not all vendors follow appropriate cybersecurity measures, which is why supply chain hacks are becoming more common.
Vendor risk management technological advancements, such as UpGuard’s Vendor Risk, now allow enterprises to continually monitor the security posture of their entire vendor network. Organizations with a broad vendor network may now commit Third-Party Risk Management to a team of world-class analysts to guarantee that no risks are missed and the best remediation strategies are implemented.